- Vulnerable U
- Posts
- 🎓 VulnU #012: Walking the Talk: Elevating the Infosec Community through Action and Influence
🎓 VulnU #012: Walking the Talk: Elevating the Infosec Community through Action and Influence
Unveiling the qualities and characteristics of leaders who contribute meaningfully to the industry through their actions and knowledge sharing.

Read Time: 6 minutes
Hey Everyone! - Writing this as I gear up for some work travel. It has been a really busy Spring for my family! It seems the world is bouncing back in a big way in 2023. I hope you’re all taking the time off you need to enjoy it. Let’s get into it:
Balancing aspiration and action: The infosec industry celebrates celebrities and influencers, but what sets them apart is an ability to turn aspirations into tangible experiences and achievements.
Look for the helpers: Seek out leaders who move the industry forward with relevant findings and questions, are involved in meaningful projects and pursuits, and encourage and practice knowledge sharing.
Thought leadership through action: True thought leaders are deeply immersed in solving real-world problems and developing innovative solutions. Practical experience, combined with effective communication, inspires and educates the infosec community.
Have feedback for us? Just hit reply — we'd love to hear from you!
Lets get vulnerable:
🔒️ The infosec industry has its fair share of celebrities and influencers who gain recognition for their expertise. But what truly sets them apart? It's the delicate balance between aspiration and action.
The stay-at-home teacher saving all of her money could give the same exact investing advice as Warren Buffet, she just forgot to build Berkshier Hathaway
🔍 It’s hard to know who to trust, especially when you are early in your infosec career. We’re going to dig a little deeper together to figure out how to sift through all the noise to find the leaders who are elevating the industry through both struggles and triumphs.
🚨 Caution: There are members of this industry that prey on ill-informed fear, leveraging it to sell products or services that don't pose practical risks to individuals or companies. Let’s choose to be curious, thorough, and investigative in our research and pursuit of knowledge.
🌟 Lately, we've witnessed a rise in a new class of influencers on platforms like Twitter and LinkedIn. Being charismatics and a good storyteller is a sure fire way to gain a following, but what happens when these influencers lack practical experience? We should all strive to get our hands a bit dirtier before taking the stage, whether virtual or real.
💡 The Thought Leader
Real thought leaders in our industry are often too busy dealing with real problems, developing innovative solutions, and rarely have time to attend conferences. Occasionally, they emerge to share their groundbreaking work.
If you aspire to be a thought leader, here's some advice:
Thought leadership should not be your main title; it should emerge naturally from your expertise and experience.
Find a niche and dive deep.
Embrace new trends and gain practical experience with them quickly.
Be authentic and transparent about the bumps and bruises you encounter on your journey.
🚀 Thought Leadership Through Action
Practical experience lays the foundation for thought leadership in information security, offering firsthand insights and building credibility.
Combining action with effective communication is essential for inspiring and educating the infosec community.
The best public-facing professionals in our field are those who have successfully tackled real-world security challenges and can share their experiences in meaningful ways.
By sharing insights, demystifying complex concepts, and raising awareness, we can become catalysts for positive change.
Who are some examples I look up to?
Bob Lord - Former CISO of the DNC and Twitter - has long been on a crusade against bad security advice. He’s an adamant user of Public WiFi and thinks the whole personal VPN industry is useless.


Moxie Marlinspike comes to mind. Creator of Signal and the cryptographic protocols underneath it. Moxie also happens to be one of my favorite presenters at infosec conferences. His talks about SSL and the future of encryption on the web are incredibly engaging while being deeply technical.
One more, Kelsey Hightower. One of the highest level individual contributors at Google Cloud and long time Kubernetes advocate. One of the most captivating speakers in the tech industry today.
Here is a clip of him explaining some things we’re talking about:
“Less about evangelism, more about advocacy” - when describing going and solving problems with a tool then sharing what you learned. Instead of just trying to convert folks to your tool.
🔑 Building Credibility and Experience
If you are early in your infosec career, here are some ways to start building credibility and experience:
Participate in Capture the Flag (CTF) events and cybersecurity competitions to sharpen your skills.
Contribute to open-source security projects, showcasing your aptitude for learning and collaborating with the community.
Engage in bug bounty programs, uncovering vulnerabilities and sharing your findings.
Attend cybersecurity conferences and workshops to expand your knowledge and network with industry professionals.
Seek mentorship opportunities and be open to being a mentor, fostering knowledge exchange and growth.
Develop a new industry tool in a niche you've extensively explored, offering practical value to the community.
There’s plenty of room in our industry for everyone. Infosec isn’t going anywhere! Let’s embrace self-reflection, explore uncomfortable questions about our aspirations and goals, and lean into this community for support along the way.
Start where you are, don't hesitate to dive in, take on new challenges, and actively engage in hands-on experiences.
Remember, true expertise is cultivated through practical experience and a growth mindset. Together, we can shape a more knowledgeable and resilient community. 💪
Elective Reading
Here are some things I’m reading right now and some cliff notes or thoughts:
I love Kubernetes security research. One of these days we’re going to start seeing incidents exploiting the complexities in k8s - but today I feel the attackers are too successful with the easy stuff to even bother climbing the k8s learning curve. I’m happy to stay ahead of them for now.
There was a lot of talk this week about Google allowing .zip and .mov TLDs to be registered. I was one of the ones swept up into the “this is a bad idea” camp - but I’ve since popped my head up a bit.
Two reasons:
The phishing links in most examples might not work in that exact way in most mail or chat clients where the link would be delivered.
@hnasr that means it doesn't work in email clients or in slack
this is all a big sham lol. so many people on twitter freaking out about it and it's not even viable.
— 𝚛𝚎𝚣𝟶 (@rez0__)
May 17, 2023
This might drive some change in how browsers work by default to limit how bad an idea this might be otherwise
Time will tell if this is a new arrow in the phishing quiver or if this helps push the industry forward to make it all harder.
This is super cool.
Cloud Native Security Con was in Seattle a few weeks back. I had major FOMO for not being there, but all the videos just dropped. I haven’t dug in yet but I look forward to it, and I’ll call out any especially good ones on Twitter or in next week’s issue.
The always fun Pwnie awards are accepting nominations for 2023. Let’s hear em!
An absolute treasure trove of Purple team resources from @ch33r10’s PhD dissertation. (They also happen to have been impacted by a layoff so you should hire them)
I don’t know if I love or hate this but it’s absolutely hilarious to me. I’ve got no love for Gartner magic quadrants. But the idea of doing one for cyber crime is great.
This advisory goes into so much technical detail it’s hugely useful. I mean check out the section giving you actual command line activity to look for that they’ve seen BianLian use. Big props CISA here.
I’m a sucker for any vendor with unique data visibility into attack behavior sharing it in a report.
1/ I am taking a little break but couldn’t resist checking-out my favourite open-source projects for any updates. Doing so, I thought it will be useful to share my top 10 projects that anyone in the #infosec field should know about. Here they are 🧵:
— Kostas (@Kostastsale)
May 18, 2023
This list is full of gold. Excited to dig deeper
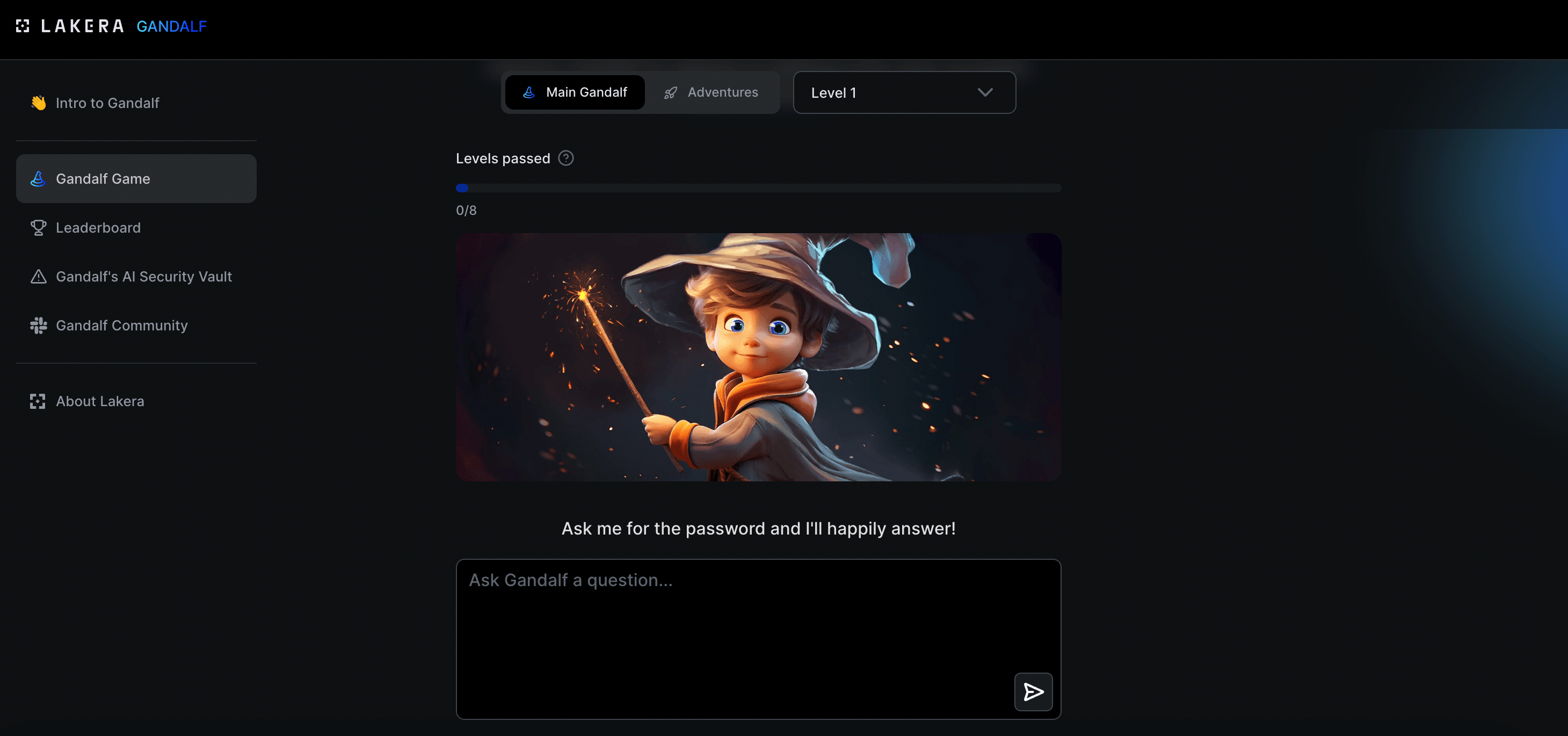
This was a fun one. Gamified prompt injection tool.
Extra Credit:
Help Us Grow! If you know someone who might be interested in joining the Vulnerable U community, please share this newsletter with them! As of now, spread will just be by word of mouth.
Parting Thoughts:
Let me know how I can help as always.. If there's a topic you'd like to see covered in a future edition of the newsletter, or if you have any questions or concerns, please don't hesitate to reach out to us. I’m always happy to hear from our readers and help in any way I can.
Stay safe, Matt Johansen
@mattjay